Secure Home Security Cameras From Cyber Threats: Protecting Your Privacy
Secure home security cameras from cyber threats is paramount in today’s digital age, where personal privacy hangs in the balance. As we delve into the world of cybersecurity for home surveillance, it’s crucial to understand the risks and best practices to keep your security intact.
Importance of Secure Home Security Cameras
Securing home security cameras from cyber threats is essential in safeguarding personal privacy and enhancing overall security within the home environment. Without proper security measures in place, unsecured cameras can pose significant risks and vulnerabilities.
Potential Risks of Unsecured Cameras
- Unauthorized access to live camera feeds, compromising privacy.
- Potential hacking of cameras to spy on residents or gather sensitive information.
- Manipulation of footage or deletion of crucial evidence in case of incidents.
Consequences of Cyber Attacks on Home Security Systems
- Exposure of personal information and daily routines to malicious actors.
- Breaches in security leading to physical break-ins or theft.
- Loss of trust in the security system and increased feelings of vulnerability.
Common Cyber Threats Targeting Home Security Cameras
- Phishing attacks targeting camera login credentials.
- Ransomware attacks locking users out of their camera systems.
- Denial of Service (DoS) attacks disrupting camera functionality.
Best Practices for Securing Home Security Cameras
- Enable two-factor authentication for an added layer of security.
- Regularly update camera firmware to patch vulnerabilities.
- Change default login credentials to unique, strong passwords.
Role of Encryption in Safeguarding Camera Footage
Encryption plays a crucial role in protecting the footage captured by security cameras, ensuring that only authorized individuals can access and view the recordings. By encrypting data, the confidentiality and integrity of the footage are preserved.
Importance of Regularly Updating Firmware
Regularly updating camera firmware is vital to enhance security and protect against known vulnerabilities. Manufacturers release updates to address security flaws and improve overall system performance, making it essential for users to stay current with the latest firmware versions.
Tips for Creating Strong Passwords
- Use a combination of letters, numbers, and special characters.
- Avoid using easily guessable information like birthdays or pet names.
- Consider using a password manager to securely store and manage passwords.
Common Cyber Threats to Home Security Cameras
Home security cameras are vulnerable to various cyber threats that can compromise personal privacy and security. Hackers often target these devices to exploit vulnerabilities for malicious purposes.
1. Phishing Attacks
Phishing attacks involve tricking users into revealing sensitive information by posing as a trustworthy entity. Hackers may send fake emails or messages to gain access to security camera systems.
2. DDoS Attacks
DDoS (Distributed Denial of Service) attacks overwhelm a network with traffic, causing it to crash. This can render security cameras inoperable, leaving the home vulnerable to physical intrusions.
3. Password Cracking
Weak passwords are an easy target for hackers to gain unauthorized access to security cameras. Once inside, they can spy on residents or tamper with the footage without detection.
4. Firmware Exploitation
Outdated firmware in security cameras can contain vulnerabilities that hackers exploit to take control of the device. This allows them to manipulate settings or disable the camera remotely.
5. Eavesdropping
Hackers can intercept the video and audio feeds from insecure security cameras, violating the privacy of individuals inside their homes. This breach of security can lead to blackmail or other illicit activities.
6. Data Breaches
If security camera footage is stored insecurely, it can be susceptible to data breaches. Hackers may steal sensitive recordings and use them for extortion, identity theft, or other criminal activities.
Preventive Measures
- Change default passwords to strong, unique ones.
- Regularly update firmware to patch security vulnerabilities.
- Enable two-factor authentication for added protection.
- Secure your home network with a strong firewall and encryption.
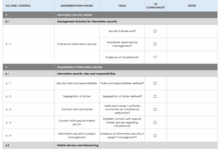
Comparison of Security Features
| Brand | Security Features |
|---|---|
| Brand A | End-to-end encryption, regular security updates |
| Brand B | Advanced motion detection, cloud storage encryption |
| Brand C | AI-powered threat detection, secure mobile app access |
Strategies for Securing Home Security Cameras
In today’s digital age, it is crucial to implement effective strategies to secure home security cameras from cyber threats. By following best practices and utilizing different security measures, you can enhance the protection of your surveillance system.
Encryption
Encryption plays a vital role in safeguarding the data transmitted between your security cameras and the monitoring device. By encrypting the communication channels, you can prevent unauthorized access to the footage. It is essential to use strong encryption protocols to ensure the confidentiality and integrity of the data.
Strong Passwords
One of the simplest yet most effective security measures is setting up strong passwords for your security cameras. Avoid using default or common passwords and opt for complex combinations of letters, numbers, and special characters. Regularly updating your passwords and avoiding password reuse across multiple devices can significantly reduce the risk of unauthorized access.
Firmware Updates
Regularly updating the firmware of your security cameras is essential to patch any vulnerabilities and enhance overall security. Manufacturers often release firmware updates to address known security issues, so it is crucial to stay up-to-date with the latest releases. Set up automatic updates whenever possible to ensure your cameras are protected against emerging threats.
Network Segregation
Segregating your home security camera system on a separate network can add an extra layer of security. By isolating your cameras from other devices on the network, you can minimize the risk of a security breach spreading across all connected devices. Implementing network segmentation can help contain potential threats and protect your surveillance system from cyber attacks.
Importance of Regular Updates for Home Security Cameras
Regular firmware updates play a crucial role in maintaining the security of home security cameras. These updates often include patches for vulnerabilities that could be exploited by cyber threats, ensuring that your cameras remain protected from potential attacks.
Risks of Running Outdated Firmware on Security Cameras
Outdated firmware on security cameras poses a significant risk as it may contain known security vulnerabilities that hackers can exploit to gain unauthorized access to your camera feed. This could lead to privacy breaches, unauthorized surveillance, or even remote control of the camera by malicious actors.
Step-by-Step Guide on How to Update Firmware of Home Security Cameras
1. Check for firmware updates on the manufacturer’s website or through the camera’s mobile app.
2. Download the latest firmware version compatible with your camera model.
3. Follow the manufacturer’s instructions to install the firmware update onto the camera.
4. Reboot the camera to apply the changes and ensure the update was successful.
Wireless vs. Physical Connection for Updating Firmware
Updating firmware wirelessly is convenient but may be less secure compared to using a physical connection. For better security, consider using a physical connection (e.g., Ethernet cable) to update the firmware, especially for critical updates that require a secure connection.
Troubleshooting Checklist for Firmware Update Issues
– Ensure the camera is connected to a stable internet connection.
– Verify that the firmware update file is compatible with your camera model.
– Restart the camera and try the firmware update process again.
– Contact customer support if the issue persists or if you encounter error messages during the update.
Recommended Frequency for Checking and Updating Firmware
| Camera Brand | Recommended Frequency |
|---|---|
| Brand A | Monthly |
| Brand B | Bi-Monthly |
| Brand C | Quarterly |
Role of Encryption in Protecting Home Security Cameras
Encryption plays a crucial role in safeguarding the data transmitted by home security cameras, ensuring that sensitive information remains secure from cyber threats.
Different Encryption Protocols for Home Security Cameras
- Transport Layer Security (TLS): Provides secure communication over a network, commonly used for encrypting video feeds from security cameras.
- Advanced Encryption Standard (AES): Widely adopted for its strong encryption capabilities, ensuring data confidentiality and integrity.
- Secure Sockets Layer (SSL): Another protocol used to establish encrypted links between web servers and browsers, enhancing security for video transmission.
Importance of End-to-End Encryption for Privacy
End-to-end encryption ensures that data is encrypted from the moment it leaves the camera until it reaches the intended recipient, maintaining privacy in home surveillance systems.
Symmetric vs. Asymmetric Encryption for Home Security Cameras
- Symmetric Encryption: Uses a single key to encrypt and decrypt data, ideal for securing video feeds in real-time monitoring.
- Asymmetric Encryption: Involves a pair of public and private keys for encryption and decryption, enhancing security but requiring more computational resources.
Setting Up Encryption for Home Security Cameras
To set up encryption for a home security camera system, follow these steps:
- Choose a strong encryption algorithm like AES.
- Generate secure encryption keys with sufficient length.
- Configure the camera settings to enable encryption for data transmission.
- Regularly update encryption protocols to address vulnerabilities and enhance security.
Potential Vulnerabilities without Proper Encryption
Failure to implement encryption properly can expose home security camera systems to various vulnerabilities, including unauthorized access to video feeds and data breaches.
Impact of Encryption on Camera Performance
While encryption adds a layer of security, it can introduce some performance overhead and latency to home security camera feeds. However, the trade-off is necessary to ensure data protection.
Securing Home Wi-Fi Networks for Camera Protection
Securing your home Wi-Fi network is crucial to prevent unauthorized access to your security cameras. Hackers can potentially gain access to your cameras through your Wi-Fi network if it is not properly secured.
Risks of Using Default Passwords on Wi-Fi Routers
Using default passwords on Wi-Fi routers for home security cameras poses a significant risk as they are easily guessable by hackers. It is important to change the default password to a strong, unique password to enhance the security of your network.
Tips for Setting Up a Secure Wi-Fi Network
- Change the default SSID of your Wi-Fi network to something unique to avoid being easily identified by hackers.
- Enable WPA2 or WPA3 encryption on your Wi-Fi network to protect the data transmitted between your cameras and the router.
- Disable remote access to your router’s administration settings to prevent unauthorized changes to your network.
- Regularly update the firmware of your router to patch any security vulnerabilities that could be exploited by hackers.
- Use a firewall to monitor and filter incoming and outgoing network traffic to protect your cameras from cyber threats.
Two-Factor Authentication for Home Security Cameras
Two-factor authentication is a security process that requires two different forms of identification to verify the user’s identity. This adds an extra layer of protection to home security camera systems, making it more difficult for unauthorized users to gain access.
Enabling Two-Factor Authentication for Popular Home Security Camera Brands
Enabling two-factor authentication for popular home security camera brands such as Ring, Arlo, and Nest is relatively straightforward. Users can usually find the option to enable this feature in the settings menu of the camera’s mobile app or web interface. By following the on-screen instructions, users can link their account to a secondary form of identification, such as a mobile phone number or email address, to complete the authentication process.
Benefits of Using Biometric Authentication Methods
Biometric authentication methods, such as fingerprint or facial recognition, provide an even more secure way to access home security cameras. These methods are unique to each individual and are difficult to replicate, making it extremely challenging for unauthorized users to bypass the authentication process. By using biometric authentication, homeowners can ensure that only authorized individuals have access to their security camera feed.
Securing Cloud Storage for Home Security Camera Footage
Securing cloud storage for home security camera footage is crucial to ensure the privacy and protection of recorded videos. By implementing strong security measures, homeowners can prevent unauthorized access to their surveillance footage and safeguard their personal data.
Importance of Securing Cloud Storage
- Choose cloud storage providers that offer end-to-end encryption for data transmission and storage to keep your footage secure.
- Regularly update your cloud storage account password and enable two-factor authentication for an added layer of security.
- Implement access controls and permissions within the cloud storage system to restrict unauthorized users from viewing or modifying your recorded footage.
Comparing Security Measures of Cloud Storage Providers
- Research and compare different cloud storage providers to assess their security features, such as encryption protocols, data protection policies, and vulnerability monitoring.
- Opt for providers with a strong track record of data security and compliance with industry standards to ensure the safety of your footage.
Encrypting Data in the Cloud
- Utilize robust encryption methods to protect your data stored in the cloud, such as AES-256 encryption, to prevent unauthorized access and data breaches.
- Encrypt sensitive files before uploading them to the cloud and securely manage encryption keys to maintain control over who can decrypt the data.
Two-Factor Authentication for Enhanced Security
- Enable two-factor authentication for your cloud storage account to require an additional verification step, such as a code sent to your phone, when accessing your footage.
- This extra layer of security helps prevent unauthorized access even if your password is compromised.
Setting Up Access Controls and Permissions
- Establish access controls within your cloud storage system to designate specific users or devices that are authorized to view or manage the recorded footage.
- Regularly review and update permissions to ensure that only trusted individuals can access the surveillance data.
Best Practices for Updating Passwords and Security Keys
- Change your cloud storage account password regularly and use a strong, unique password that is not easily guessable.
- Rotate security keys and credentials associated with your cloud storage to minimize the risk of unauthorized access and data leaks.
Benefits of End-to-End Encryption
- End-to-end encryption ensures that only authorized parties can access and decrypt your home security camera footage stored in the cloud, adding an extra layer of protection against potential breaches.
- By encrypting your data from end to end, you can maintain the confidentiality and integrity of your surveillance footage, even in the event of a security breach.
Privacy Concerns with Smart Home Security Cameras
Smart home security cameras provide a sense of security and peace of mind, but they also raise privacy concerns due to the data they collect and potential misuse of that data.
Privacy Issues with Smart Home Security Cameras
- Unauthorized Access: Hackers can gain access to the camera feed and spy on individuals inside the home.
- Data Breaches: Personal information and footage captured by the cameras can be stolen in a data breach.
- Third-Party Sharing: Some security camera companies may share or sell user data to third parties without consent.
Minimizing Privacy Risks with Smart Home Security Cameras
- Secure Passwords: Use strong, unique passwords for camera accounts to prevent unauthorized access.
- Regular Updates: Keep camera firmware up to date to patch security vulnerabilities and protect against cyber threats.
- Privacy Settings: Review and adjust privacy settings on the camera app to control data sharing and access permissions.
- Local Storage: Opt for cameras with local storage options to keep footage within the home network instead of cloud storage.
- Disable Remote Access: Turn off remote access to the camera when not needed to reduce the risk of unauthorized viewing.
Best Practices for Remote Access to Home Security Cameras
When it comes to accessing home security cameras remotely, it is crucial to do so in a secure manner to prevent any cyber threats or unauthorized access to your system.
Secure Remote Access Guidelines
- Use a Virtual Private Network (VPN): Set up a VPN to create a secure connection to access your home security cameras remotely.
- Enable Two-Factor Authentication: Implement two-factor authentication to add an extra layer of security to your remote access login process.
- Update Firmware Regularly: Keep your security cameras’ firmware up to date to patch any vulnerabilities that could be exploited by hackers.
- Use Strong Passwords: Ensure your passwords for accessing the cameras remotely are strong and unique to prevent brute force attacks.
- Limit Access Permissions: Only grant remote access to trusted users and regularly review access permissions to minimize the risk of unauthorized entry.
Securing Mobile Apps for Home Security Cameras
In today’s digital age, mobile apps play a crucial role in controlling and monitoring home security cameras. However, with this convenience comes the responsibility of ensuring the security of these apps to prevent unauthorized access to your surveillance system.
When using mobile apps to control home security cameras, it is essential to consider the following security aspects:
Security Considerations for Mobile Apps
- Always download apps from official app stores to minimize the risk of downloading malicious software.
- Regularly update the mobile app to patch any known vulnerabilities that could be exploited by cybercriminals.
- Avoid connecting to public Wi-Fi networks when accessing the security camera system through the mobile app to prevent eavesdropping.
Risks of Vulnerabilities in Mobile Apps
- Mobile apps connecting to security camera systems may contain vulnerabilities that could be exploited by hackers to gain unauthorized access.
- Outdated mobile apps may have security flaws that cybercriminals can exploit to compromise the security of your home surveillance system.
Tips for Enhancing Mobile App Security
- Use strong, unique passwords for both the mobile app and the security camera system to prevent unauthorized access.
- Enable two-factor authentication for an added layer of security, requiring a verification code in addition to the password.
- Regularly update the mobile app and security camera firmware to patch any known vulnerabilities and ensure optimal security.
Importance of Secure Wi-Fi Network
- Using a secure Wi-Fi network is crucial to prevent unauthorized access to your security camera system through the mobile app.
- Secure your Wi-Fi network with a strong password and encryption to protect the data transmitted between the app and the security cameras.
Importance of User Awareness and Education for Home Security
In the realm of securing home security cameras from cyber threats, user awareness and education play a crucial role in ensuring the safety and privacy of your surveillance system. By educating users about potential risks and best practices, individuals can take proactive steps to protect their home security cameras from malicious attacks.
Preventing Social Engineering Attacks
User awareness is vital in preventing social engineering attacks that specifically target security camera systems. Cybercriminals often use social engineering tactics to manipulate users into revealing sensitive information or granting access to their devices. By understanding how these attacks work and being cautious of suspicious requests or communications, users can thwart potential threats to their home security cameras.
- Regularly educate yourself on common social engineering techniques, such as phishing emails or phone scams.
- Be cautious of unsolicited requests for personal information or login credentials related to your security cameras.
- Implement strong password practices and avoid sharing sensitive details with unverified sources.
Resources for Cybersecurity Practices
To stay informed about the latest cybersecurity practices for home surveillance, users can leverage various resources available online. These platforms offer valuable insights, tips, and updates on securing home security cameras against cyber threats.
- Follow reputable cybersecurity blogs and websites that specialize in home security and surveillance technology.
- Attend webinars or online workshops that focus on cybersecurity awareness and best practices for protecting home devices.
- Engage with online communities or forums dedicated to home security to exchange knowledge and learn from other users’ experiences.
Integrating Home Security Cameras with Smart Home Devices
Integrating home security cameras with smart home devices can enhance the overall functionality and convenience of your home automation system. However, this interconnected setup also brings security implications that need to be addressed to ensure the safety and privacy of your household.
Security Implications of Integrating Security Cameras with Smart Home Devices
Integrating security cameras with other smart home devices can create potential vulnerabilities in your network. Hackers can exploit these interconnected devices to gain access to your camera feeds, compromising your privacy and security. It is crucial to take necessary precautions to secure your smart home ecosystem.
- Ensure all smart devices, including security cameras, are running the latest firmware and security patches to mitigate potential vulnerabilities.
- Implement strong, unique passwords for each device to prevent unauthorized access.
- Enable two-factor authentication whenever possible to add an extra layer of security to your smart home system.
- Regularly monitor your network for any suspicious activity that may indicate a security breach.
Tips for Securely Integrating Security Cameras into a Smart Home Ecosystem
When integrating security cameras into your smart home ecosystem, consider the following tips to enhance the security of your setup:
- Segment your network to create isolated zones for your smart devices, including security cameras, to prevent potential lateral movement by cyber attackers.
- Use a secure Wi-Fi network with strong encryption protocols to safeguard the communication between your devices.
- Limit the number of third-party apps and services that have access to your security camera feeds to minimize the risk of data exposure.
- Regularly review and update your privacy settings to ensure that only authorized users have access to your camera footage.
Interconnected Smart Home Devices and Security Risks to Home Security Camera Systems
The interconnected nature of smart home devices can introduce security risks to your home security camera systems. If one device within your smart home ecosystem is compromised, it can potentially open up access to your security cameras as well. It is essential to establish robust security measures to protect all interconnected devices and prevent unauthorized access to your camera feeds.
Testing the Security of Home Security Camera Systems
The security of home security camera systems is crucial in ensuring the safety and privacy of individuals and their property. Conducting security tests on these systems is essential to identify vulnerabilities that could be exploited by cyber attackers.
Importance of Security Assessments for Home Security Cameras
- Performing security assessments helps in proactively identifying weaknesses in the security of home security camera systems.
- It enables homeowners to take necessary measures to strengthen the security of their surveillance systems before any cyber threats occur.
- Regular security testing ensures that home security cameras are equipped to withstand evolving cyber threats and attacks.
How to Perform Security Assessments and Penetration Testing
- Utilize ethical hacking techniques to simulate cyber attacks and identify vulnerabilities in home security camera systems.
- Engage with cybersecurity experts or professionals to conduct thorough security assessments and penetration testing.
- Employ automated vulnerability scanning tools to detect common security issues in home security camera systems.
Common Vulnerabilities and How to Address Them
- Default credentials: Change default usernames and passwords to unique and strong credentials to prevent unauthorized access.
- Outdated firmware: Regularly update the firmware of home security cameras to patch known vulnerabilities and enhance security.
- Weak encryption: Ensure that data transmission from security cameras is encrypted to protect against interception and tampering.
Setting Up a Controlled Environment for Security Testing
- Establish a separate network for testing purposes to prevent accidental exposure of sensitive data during security assessments.
- Use virtualized environments or sandboxing techniques to create a controlled testing environment for home security camera systems.
Tools and Software for Security Assessments
- Popular tools like Nessus, Metasploit, and Nmap can be used to perform vulnerability scanning and penetration testing on home security camera systems.
- Security professionals can leverage Wireshark for network packet analysis to identify potential security gaps in surveillance systems.
Legal and Ethical Considerations in Security Testing
- Ensure compliance with relevant laws and regulations when conducting security tests on home security camera systems to avoid legal repercussions.
- Obtain explicit consent from homeowners before conducting security assessments to maintain ethical standards and respect privacy rights.
Best Practices Based on Security Test Findings
- Implement multi-factor authentication for accessing home security camera systems to add an extra layer of security.
- Regularly monitor and audit system logs to detect and respond to any suspicious activities or unauthorized access attempts.
Final Summary
From encryption to firmware updates, securing your home security cameras is not just about technology—it’s about safeguarding your peace of mind. Stay informed, stay vigilant, and keep your home safe from cyber threats.